The Washington Post is warming up an old crypto story:
For more than half a century, governments all over the world trusted a single company to keep the communications of their spies, soldiers and diplomats secret.
The company, Crypto AG, got its first break with a contract to build code-making machines for U.S. troops during World War II. Flush with cash, it became a dominant maker of encryption devices for decades, navigating waves of technology from mechanical gears to electronic circuits and, finally, silicon chips and software.
The Swiss firm made millions of dollars selling equipment to more than 120 countries well into the 21st century. Its clients included Iran, military juntas in Latin America, nuclear rivals India and Pakistan, and even the Vatican.
But what none of its customers ever knew was that Crypto AG was secretly owned by the CIA in a highly classified partnership with West German intelligence. These spy agencies rigged the company’s devices so they could easily break the codes that countries used to send encrypted messages.
The decades-long arrangement, among the most closely guarded secrets of the Cold War, is laid bare in a classified, comprehensive CIA history of the operation obtained by The Washington Post and ZDF, a German public broadcaster, in a joint reporting project.
That Crypto AG had been a CIA/NSA/BND operation has been known for decades. One wonders why the CIA history was now leaked to the Washington Post and to the German state TV channel ZDF.
Scott Shane @ScottShaneNYT – 14:38 UTC · Feb 11, 2020
Back in 1995 at the @baltimoresun, with @TBowmanNPR, I wrote a long story on the NSA’s covert relationship with Crypto AG, allowing the US to read the secrets of many countries: link. Now @gregpmiller got the official CIA history of this decades-long project.
Greg’s story is a fascinating read on what we described in 1995 as one of the great intelligence operations of the Cold War filling in details we could only guess at 25 years ago. I’m glad to see we got the story right.
I recall vividly how at the end of my trip to Switzerland in 1995 to find former employees of Crypto AG, one of them managed to find a smoking-gun memo from 1975 that showed an NSA crypto mathematician named Nora Mackebee had attended a Crypto design meeting.
Two years after Scott Shane broke the story Wayne Madsen basically plagiarized it to write a similar story for some conspiracy lovers magazine:Sanho Tree @SanhoTree – 13:48 UTC · Feb 11, 2020
For the record, I published the Crypto AG story 23 years ago when I was an editor at Covert Action Quarterly.
If you want to understand why the US intelligence community is so freaked out about Huawei, it’s because they’ve been playing the same game for decades. Crypto AG: The NSA’s Trojan Whore?
—Scott Shane @ScottShaneNYT – 15:05 UTC · Feb 11, 2020
Replying to @SanhoTree
And for the record, the CAQ story from 1997 relied mainly on the @baltimoresun story I wrote with @tbowman in 1995: RIGGING THE GAME
The Swiss company Crypto AG became useless for the NSA when people moved to standard computers to encrypt their information and used the Internet to send it. It needed some other companies it could manipulate.
Around that time this writer was the chief technical officer of a large Internet access company. When we had to select a firewall platform for our internal networks we cynically discussed if it would be preferable to buy Cisco equipment, to then be spied on by the NSA, or to buy from the Israeli company Checkpoint which likely had a Mossad backdoor. (We bought both and stacked them.)
That such cynicism was wholly justified became evident when Edward Snowden revealed the NSA machinations. Soon thereafter Juniper Networks, a provider of large backbone equipment, was found to have at least two NSA backdoors in its operation system. Other ‘western’ telecommunication equipment companies were similarly manipulated:
Even neutral countries firms are not off-limits to NSA manipulations. A former Crypto AG employee confirmed that high-level US officials approached neutral European countries and argued that their cooperation was essential to the Cold War struggle against the Soviets.
The NSA allegedly received support from cryptographic companies Crypto AG and Gretag AG in Switzerland, Transvertex in Sweden, Nokia in Finland, and even newly-privatized firms in post-Communist Hungary.
In 1970, according to a secret German BND intelligence paper, supplied to the author, the Germans planned to “fuse” the operations of three cryptographic firms-Crypto AG, Grattner AG (another Swiss cipher firm), and Ericsson of Sweden.
So why was the allegedly secret CIA history of an already known story leaked right now? And why was it also leaked to a German TV station?
Sanho Tree points to the likely reason:
If you want to understand why the US intelligence community is so freaked out about Huawei, it’s because they’ve been playing the same game for decades.
The WaPo story itself also makes that connection:
There are also echoes of Crypto in the suspicions swirling around modern companies with alleged links to foreign governments, including the Russian anti-virus firm Kaspersky, a texting app tied to the United Arab Emirates and the Chinese telecommunications giant Huawei.
The warmed up Crypto AG story is a subtle smear piece against Huawei and Kapersky.
The U.S. wants to convince European countries to not buy Huawei products for their 5G networks. It wants to remind them that telecommunication products can be manipulated. It wants to instill fear that China would use Huawei to spy on foreign countries just like the U.S. used Crypto AG.
This is also the reason for this recent misleading Reuters headline which the story itself debunked:
Germany has proof that Huawei worked with Chinese intelligence: Handelsblatt
“At the end of 2019, intelligence was passed to us by the U.S., according to which Huawei is proven to have been cooperating with China’s security authorities,” the newspaper quoted a confidential foreign ministry document as saying.
‘U.S. intelligence’ that is handed over to manipulate someone is of course not ‘proof’ for anything.
The U.S. is pressing its allies on a very high level:
Secretary of State Mike Pompeo declared the Chinese Communist Party “the central threat of our times” on Thursday, even as he sought to talk up the prospects of a United States trade deal with Britain, which rebuffed American pressure to ban a Chinese company from future telecommunications infrastructure.
The scathing criticism of the Chinese government was the strongest language Mr. Pompeo has used as the Trump administration seeks to convince American allies of the risks posed by using equipment from Huawei, a Chinese technology giant.
A week after Pompeo’s panic message Trump took to the phone to convince Boris Johnson who was not impressed:
Donald Trump’s previously close relationship with UK Prime Minister Boris Johnson looks close to collapse, following new revelations that the president slammed down the phone on him.
Trump’s behaviour during last week’s call was described by officials as „apoplectic,“ and Johnson has now reportedly shelved plans for an imminent visit to Washington.
…
The call, which one source described to the Financial Times as „very difficult,“ came after Johnson defied Trump and allowed Chinese telecoms company Huawei the rights to develop the UK’s 5G network.
Trump’s fury was triggered by Johnson backing Huawei despite multiple threats by Trump and his allies that the United States would withdraw security co-operation with the UK if the deal went ahead.
Trump’s threats reportedly „irritated“ the UK government, with Johnson frustrated at the president’s failure to suggest any alternatives to the deal.

Huawei products are pretty good, relatively cheap and readily available. They are just as buggy as the products of other equipment providers.
The real reason why the U.S. does not want anyone to buy Huawei products is that it is the one large network company the U.S. can not convince to provide it with backdoors.
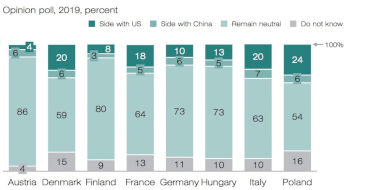
European countries do not fear China or even Chinese spying. They know that the U.S. is doing similar on a much larger scale. Europeans do not see China as a threat and they do not want to get involved in the escalating U.S.-China spat:
“Whose side should your country take in a conflict between the US and China?”
The U.S. just indicted four Chinese military officers for the 2017 hacking of Equifax during which millions of addresses and financial data were stolen. The former CIA Director General Michael Hayden had defended such pilfering as “honorable espionage” and Equifax had made it laughably easy to get into its systems:
[J]ust five days after Equifax went public with its breach — KrebsOnSecurity broke the news that the administrative account for a separate Equifax dispute resolution portal catering to consumers in Argentina was wide open, protected by perhaps the most easy-to-guess password combination ever: “admin/admin.”
To indict foreign military officers for spying when they simply pilfered barely protected servers is seen as offensive. What will the U.S. do when China does likewise?
Every nation spies. It is one of the oldest trades in this world. That the U.S. is making such a fuss about putative Chinese spying when it itself is the biggest sinner is unbecoming.
This article was published by “Moon Of Alabama”
The 21st Century